Blog Posts
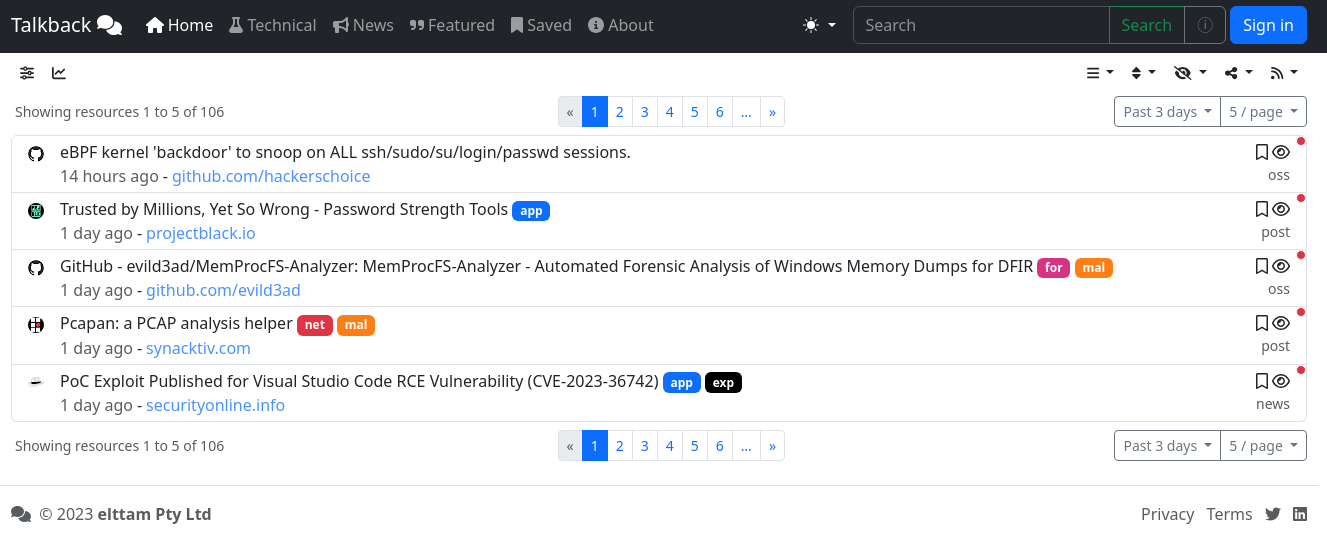
This post provides an overview of Talkback, a smart infosec resource aggregator. The post details how the system works, steps through some of its key features, and also presents how to use the UI and GraphQL API.
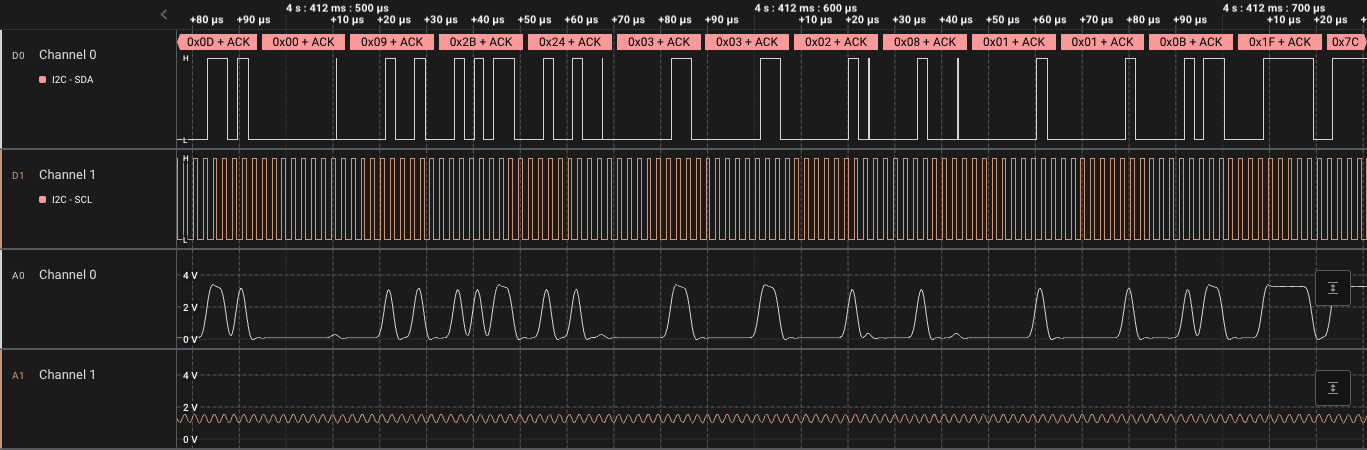
Using a sample application, this blog post gives a walkthrough of the I2C communication between the STSAFE-A110 secure element and a host MCU. A tool is released to aid in understanding the I2C flow using a logic analyser.
This blog post provides a walk-through of ESP32 firmware extraction and analysis to understand the technical implementation of the Litter Robot 3.